Radical Resilience to Keep Your Business Running
In the context of radical resilience, innovation and creativity play a crucial role. Individuals and communities are actively exploring new ideas, technologies, and approaches to problem solving. This proactive stance allows them to navigate challenges with resourcefulness and ingenuity.
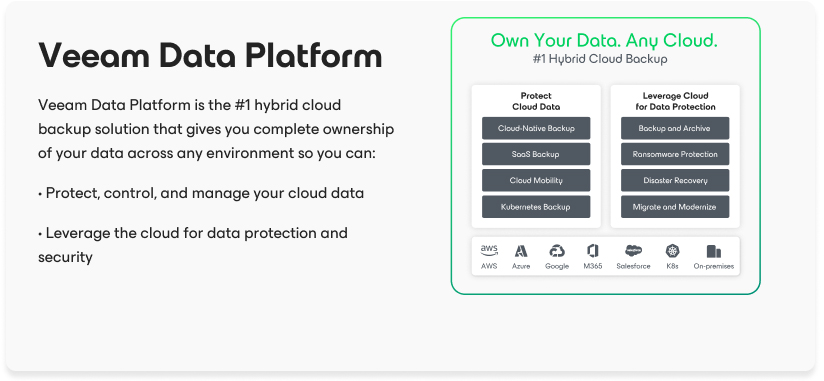
We enable organizations to complete their cyber resiliency strategy with best-in-class data security, data recovery, and data freedom.

Data Security
Multi-layered protection designed for peace of mind across the hybrid cloud.

Data Recovery
Fast, reliable recovery when you need it, where you need it.

Data Freedom
Protect all your data, anywhere, any way, with zero lock-in.
Backup Is Your Best Line of Defense
When your data is compromised or destroyed, your backups are your best line of defense. As a direct result, your backups are now the prime target of cybercriminals, making this an existential threat to your business, creating the unfortunate reality that:
- Unlike a flood or a fire, a bad actor is actively working against you
- Backup repositories are the most targeted during attack
- Compromised backups are rendered completely unusable
Secure Backup is Critical to Cyber Resiliency
Cyber resiliency is particularly crucial in the context of dealing with ransomware attacks, since recovering from an attack isn't easy. At VirtualIT, we prioritize Cyber Resiliency. We make sure that everything we do will help you successfully back up and secure your data so you can get back into production after a crisis.
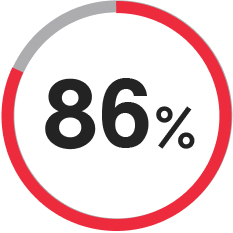
of organizations can't recover quickly enough to achieve full productivity
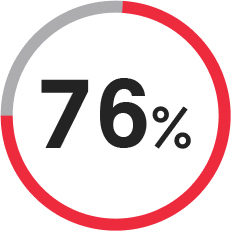
of orgs have gaps between data backup frequency vs. acceptable data loss
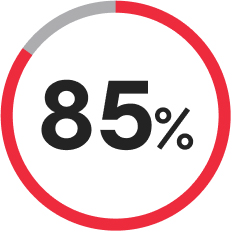
of companies experienced at least one ransomware attack in the past year
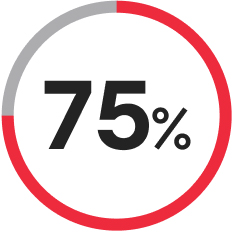
of victims stated that their backup repositories were affected
RANSOMWARE RECOVERY
Veeam's Approach to Ransomware
Ensure swift recovery with replicas, snapshots. and high-speed repositories for meeting RTOs, avoid data re-infection with YARA analysis, and streamline tasks through automated documentation, testing and verification.
Relentless Security
New features like early detection, SIEM integration and proactive threat hunting, coupled with Veeam's immutability, backup verification, and secure access, create a robust and relentless security approach.
Reduce Your Attack Surface
Harden your infrastructure with Security & Compliance Analyzer and data best practices while monitoring for errors and anomalies. I/O Anomaly Visualizer ensures the lowest possible data loss thanks to Veeam CDP.
Recover From Anywhere, to Anywhere
Meet your RTOs while ensuring you avoid reinfection with YARA content analysis. Let automation take the wheel for time-intensive tasks like documentation, testing, and verification so that you con restore your data from anywhere and back to product 5x faster.
Veeam Keeps Your
Backups Secure From
Ransomware
LEARN MOREClouds are Just as Susceptible to Ransomware Attacks
Nowadays, organizations are asking themselves how many clouds are necessary. They wonder how their IT teams will manage all their clouds while ensuring cyber security prevention, data protection, and other tasks.
LEARN MORE